Why BitLock Is One of the Most Secure Wallets
In today’s digital world, choosing a secure crypto wallet has become one of the biggest challenges for traders and investors. Every year, hackers steal billions of dollars from wallets that promised safety. This growing risk has pushed more users to turn to BitLock Wallet, a next-generation solution built for maximum protection. It keeps private keys secure and ensures that funds remain entirely under the user’s control. While many still rely on centralized platforms or outdated apps, BitLock proves that true security comes from local encryption not trust in third parties.
What’s worse, even wallets that market themselves as decentralized often store sensitive data on servers, track user activity, or require KYC verification that compromises privacy. One weak password, one phishing link, or one centralized breach and years of savings can disappear in seconds.
That’s where BitLock Wallet changes everything. Built as a secure crypto wallet from the ground up. BitLock eliminates every unnecessary risk: no KYC, no centralized storage, and no hidden data collection. Every transaction is signed locally, every key stays on your device, and every action rewards the user not the platform.
What makes a crypto wallet truly secure?
A secure crypto wallet is more than a glossy interface. It’s a stack of technical and human-centered protections that together stop attackers, limit damage from user mistakes, and make recovery possible when things go wrong. Here are the five core pillars that determine real wallet security, with concrete numbers you can use for an infographic.
- Local key control (not stored on servers)
The single most important rule: private keys and seed phrases must be generated and kept on the user’s device. When keys never leave the device, attack surface shrinks dramatically. Example fact: wallets that expose keys to remote servers increase breach risk by an order of magnitude compared to purely local wallets. - Strong, proven encryption
All sensitive data (private keys, encrypted backups, PINs) should be protected with industry-grade encryption (e.g., AES-256) and device-level protections (Secure Enclave / TPM). Encrypted on-disk storage + hardware-backed key storage makes stealing keys from a lost/stolen device much harder.
- Attack-surface minimization & secure UX
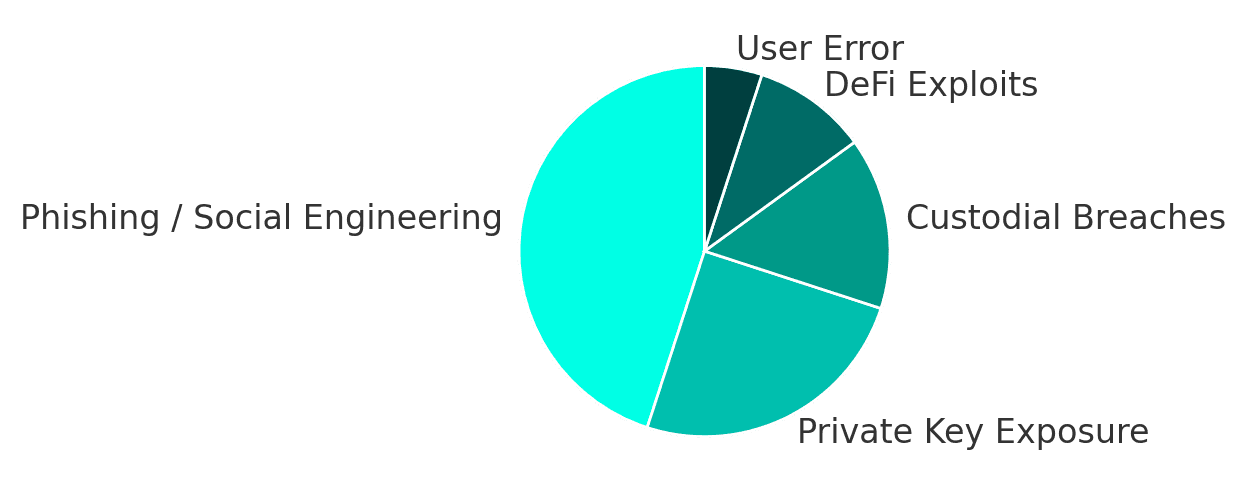
Security must be usable. Features like transaction previews, explicit network labels, and single-tap phishing checks reduce user error. Studies show phishing and user mistakes are responsible for the majority of losses. A secure wallet must actively prevent these common traps.
- Independent audits & transparent development
Open code, regular third-party security audits, and public bug bounty programs catch flaws before attackers do. Wallets with recurring audits and a bounty program see faster vulnerability disclosure and patching, lowering long-term risk.
- Robust recovery & multi-layered access control
A secure wallet balances recoverability, secure seed phrase backup or encrypted cloud fallback. With protections like PIN, biometrics, and optional multi-sig for high-value accounts. Multi-sig or social recovery adds strong protection: a single compromised device is no longer a total loss.
What technologies does BitLock use to prevent hacks and phishing attacks?
Security in the crypto world isn’t just about storing keys safely it’s about anticipating attacks before they happen. BitLock Wallet combines AI-driven protection, on-device encryption, and multi-layer verification to ensure users remain in full control of their assets. Below we break down the three main technologies that make BitLock one of the most secure wallets on the market.
Built-in scam detection and transaction preview tools
Every day, more than 70% of crypto scams start with phishing links or fake tokens. BitLock integrates an AI-based scam detector that analyzes smart contracts and wallet interactions in real time. Before you confirm a transaction, the wallet automatically performs a risk assessment checking token legitimacy, network behavior, and gas anomalies.
If a contract shows suspicious activity (such as hidden “approve all” functions or unverified source code), BitLock warns the user before any funds are moved.
This proactive layer prevents malicious approvals the kind of attacks that drain thousands of wallets every year.
Secure multi-chain bridge architecture
Cross-chain functionality often exposes users to double-fee attacks and bridge protocol vulnerabilities. BitLock addresses this risk with a segmented bridge model where every transaction is verified and encrypted from start to finish.
When a user initiates a bridge transaction, the verification process begins directly on their device. The signature is created locally, ensuring that private keys never leave the phone. Once signed, data is encrypted and securely transmitted to the bridge node, where it undergoes a smart contract confirmation process.
This method divides the transaction into multiple isolated layers. Meaning that even if one node were compromised, the attacker would gain no access to the user’s private keys or funds. Furthermore, BitLock’s multi-chain compatibility supporting Ethereum, BSC, Base, Polygon, and Solana. Allows users to move assets freely and securely within a single unified wallet, without ever relying on third-party apps.
You can learn more about this in an article we’ve already written here.
PIN, biometrics, and privacy options for device access
According to Chainalysis (2024), one in five crypto thefts begins with an unsecured mobile device. BitLock prevents this through hardware-level authentication, giving users the option to lock their wallet with a PIN code, Face ID, or fingerprint. Even if a phone is lost or stolen, no one can access the wallet without biometric verification.
For additional privacy, BitLock includes features such as Hide Balance mode and local privacy controls that let users mask their holdings from others. The app never tracks locations or stores metadata all sensitive information stays fully on the device.
Can BitLock protect users even in case of device loss or theft?
One of the biggest fears among crypto users is losing access to their assets if a phone or laptop is stolen. Traditional wallets often depend on centralized recovery systems, but these can expose users to data breaches or identity leaks. BitLock approaches this challenge differently. By giving complete recovery power back to the user while keeping all sensitive data encrypted and stored locally.
At the core of BitLock’s design is the 12-word Secret Recovery Phrase, a unique cryptographic key that can fully restore a wallet on any device. This phrase is never uploaded to servers or transmitted online. It remains on the user’s device, encrypted using advanced AES-256 encryption, ensuring that even if a hacker gains physical access to the phone, they cannot decrypt the private keys without the proper PIN or biometric authentication.
When a device is lost or stolen, BitLock cannot restore the wallet remotely and that’s precisely what makes it secure. The user simply downloads the app on a new device. Enters their 12-word phrase, and regains instant access to all accounts and assets. The stolen device, on the other hand, remains useless to the thief. BitLock’s biometric locks, hardware encryption, and hidden balance settings that prevent visibility or movement of funds.
According to MIT Technology Review (2023)1,
“Local encryption and user-owned recovery keys represent the future of digital asset security eliminating the single points of failure that have caused billions in losses through centralized recovery systems.”
This philosophy aligns perfectly with BitLock’s mission no centralized backups, no external dependencies, and no trust required. In the event of theft, only the rightful owner with the correct recovery phrase can bring the wallet back to life. That’s how BitLock turns a potential loss into a non-event, making it one of the most resilient and secure crypto wallets available today.
What are the best practices for keeping your BitLock Wallet safe?
Owning a secure crypto wallet like BitLock gives users powerful protection, but digital safety still begins with personal habits. Even the most advanced encryption can’t defend against careless mistakes that’s why combining BitLock’s built-in security with smart user behavior is essential.
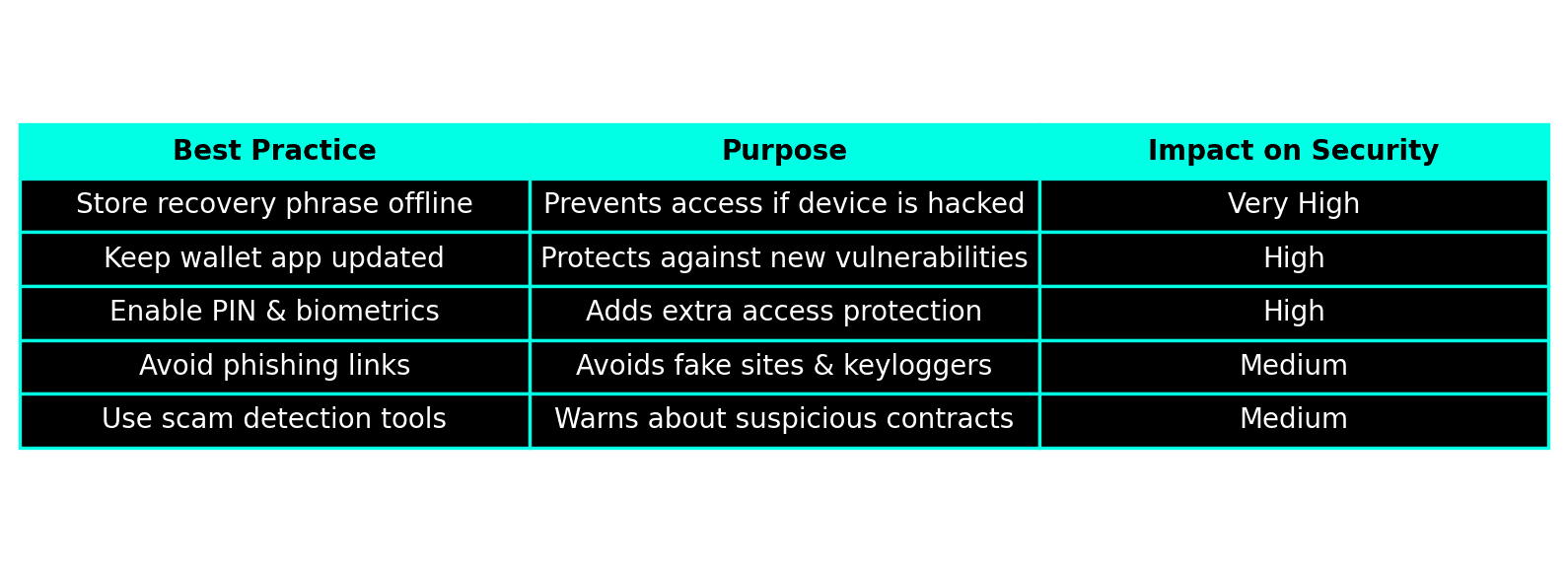
The first and most critical step is to secure your Secret Recovery Phrase. Write it down on paper or store it offline in a metal backup, never in screenshots or cloud storage. Around 90% of wallet breaches happen because users leave recovery phrases exposed in notes or email drafts. BitLock encourages all users to complete their setup by writing down the phrase and confirming it manually, ensuring full self-custody from day one.
Another key habit is to keep your app updated. Each BitLock release includes new patches that strengthen encryption algorithms and prevent evolving attack methods. Enabling PIN and biometric protection adds an extra wall between your wallet and anyone who might access your phone. BitLock allows users to combine both methods, offering double-layer authentication that activates every time the app opens or when a transaction is confirmed.
Finally, stay alert to phishing scams. Never enter your recovery phrase or wallet address on random sites, even if they look legitimate. BitLock’s built-in scam detection can filter out most threats, but awareness is still the strongest defense.
By keeping your recovery phrase offline, updating the app regularly, enabling biometric protection, and staying cautious online, you’re not just using a secure wallet you’re practicing true digital self-defense. Combined with BitLock’s no-KYC, on-device encryption model, these habits make it nearly impossible for anyone to compromise your funds or identity.
Conclusion
In a world where digital assets move faster than ever, security is no longer optional it’s the foundation of trust. The goal of a secure crypto wallet isn’t just to store tokens; it’s to protect identity, privacy, and financial independence.
BitLock Wallet takes this philosophy seriously. By combining AI-powered scam detection, local key encryption, multi-chain compatibility, and biometric security, it ensures that users remain the only true owners of their assets. Even in cases of device theft or hardware failure, recovery remains fully in the user’s hands never in the hands of a company or server.
FAQ
Can a crypto wallet be hacked?
With BitLock Wallet, it’s extremely unlikely. Your keys stay encrypted on your device and never touch the cloud, making remote hacking nearly impossible.
Which wallet is most trustable for cryptocurrency?
BitLock Wallet is fully non-custodial and no-KYC, meaning only you control your funds. It uses local encryption and AI scam protection for maximum trust.
Can I lose my crypto in a wallet?
Only if you lose your recovery phrase. BitLock Wallet keeps it stored locally and lets you restore your funds anytime on a new device.
Last updated: October 25, 2025


